SSO for Okta
This page walks you through the steps to configure Zus SSO if your organization uses Okta as your IDP.
Before you begin
- As a requirement for configuring Zus SSO, customers must attest that multi-factor authentication is required for all users and included in their identity provider's authentication workflow when accessing the Zus domain.
- Only customer users with corresponding Zus auth accounts will be accepted for SSO login.
Configuring SSO
- Go to the Okta admin console.
- Under Applications -> Applications -> click Create App Integration. Select OIDC and Web Application.
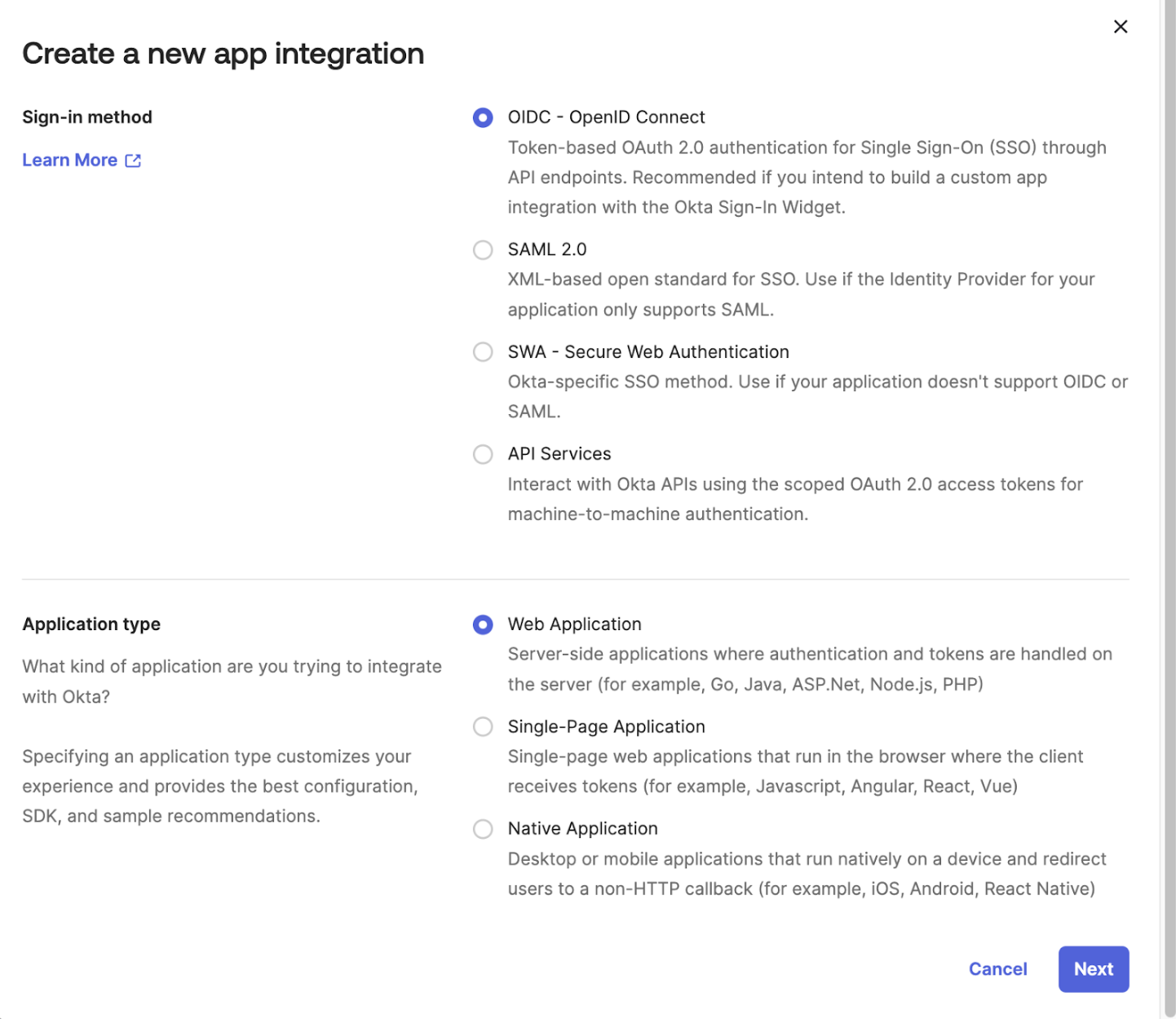
- Create a name for the app (e.g. “zus-sandbox”), and set the Sign-In Redirect URI as follows:
- Sandbox: auth.sandbox.zusapi.com/login/callback
- Production: auth.zusapi.com/login/callback
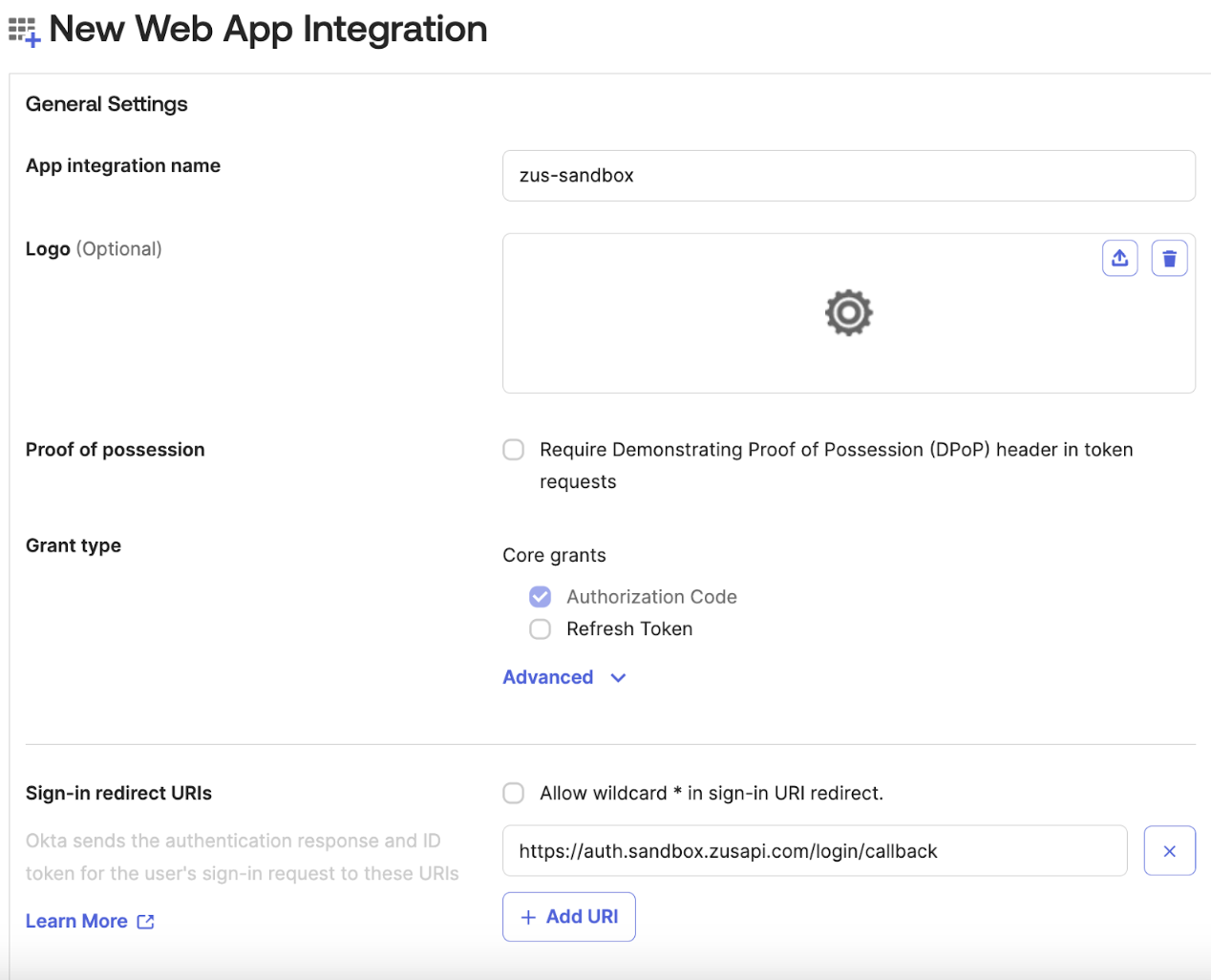
- Once you save this page, your Client ID and Client Secret will be created for you
- Share the Client ID and secret with Zus via a secure channel, along with your Okta domain (e.g. “acme.okta.com”)
Updated 3 months ago
